EggSandwich – An Egghunter with Integrity

Introduction A while back I introduced the EggSandwich in my tutorial on Egghunting as a means to implement some basic integrity checks into the traditional Egghunter and overcome the problem of fragmented / corrupted shellcode. I recently took the opportunity to update my implementation so it could accomodate shellcode of any size. The code and a brief explanation follows. What is the EggSandwich? I ran into a situation when developing an exploit for an…
Read more...Exploiting MS14-066 / CVE-2014-6321 (aka “Winshock”)
are closed
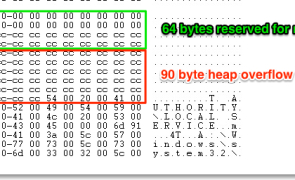
Introduction I think enough time has passed now to provide a little more detail on how to exploit MS14-066 schannel vulnerability (aka “Winshock”). In this post I won’t be providing a complete PoC exploit, but I will delve into the details on exactly how to trigger the heap overflow along with some example modifications to OpenSSL so you can replicate the issue yourself. This vulnerability was announced while I was on…
Read more...Windows Exploit Development – Part 7: Unicode Buffer Overflows
are closed
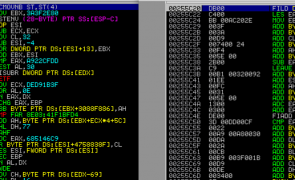
Introduction In this seventh installment of the Windows Exploit Development Series, I’ll introduce Unicode Buffer Overflows. We’ll start with a brief introduction to Unicode (what it is and why/how it’s used in Windows) and then jump right in to some example exploits. If you plan on following along, I recommend you have the following: A Windows environment (XP or Win 7 — my demos will be on the latter) Metasploit, Alpha2 or…
Read more...Tags:allplayer , alpha2 , alpha3 , ansi , ascii , bladeapimonitor , buffer overflow , debugger , dumpbin , exploit , immunity , Microsoft , perl , seh , shellcode , structured exception handler , structured exception handling , unicode , utf-16 , utf-8 , venetian , venetian shellcode , win32 , windows
Fun With Teensy
are closed

Introduction I’ve been wanting to write about the Teensy and its application in security testing or some time now. It’s extremely useful for executing scripts on a target machine without the need for human-to-keyboard interaction. It can be used to bypass auto-run, AV scanning, and encryption policies commonly targeting removable media devices in an enterprise environment. I’ve used it in my security testing to run recon/enumeration scripts, execute reverse shells, exploit local…
Read more...Tags:av bypass , dip switch , exploit , linux , mac , Microsoft , Offsec , penetration testing , pentesting , reverse shell , symantec , teensy , windows
Windows Exploit Development – Part 6: SEH Exploits
are closed
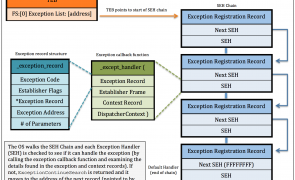
Introduction The buffer overflow exploits covered so far in this tutorial series have generally involved some form of direct EIP overwrite using a CALL or JMP instruction(s) to reach our shellcode. Today we’ll take a look at a different approach using Windows Structured Exception Handling (SEH). Before I begin explaining the basic mechanics of Windows Structured Exception Handling (as it’s implemented in an x86, 32-bit environment) it bears mentioning that…
Read more...Windows Exploit Development – Part 5: Locating Shellcode With Egghunting
are closed
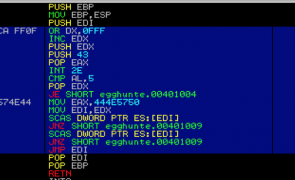
Overview In Part 4 we looked at how to find and execute your shellcode using various jump methods. In Part 5 we’re going to look at another method to find your shellcode called Egghunting. This method is especially useful when you’re faced with a small, reachable buffer (in which you can execute code) but the placement of your larger shellcode in memory is unpredictable. This post will get into quite…
Read more...Tags:coolplayer , egg sandwich , egghunter , egghunting , exploit , exploit development , omelette , shellcode , windows
Windows Exploit Development – Part 3: Changing Offsets and Rebased Modules
are closed

Overview In Part 2 we constructed a basic stack based overflow exploit for ASX To MP3 Converter. As I indicated in that post, the exploit itself is far from perfect. Successful EIP overwrite is influenced by the file path of the m3u file. In addition, although application modules are preferred when selecting jump/call addresses, the application DLL we used was rebased, meaning the address to our CALL EBX instruction is…
Read more...Windows Exploit Development – Part 1: The Basics
are closed
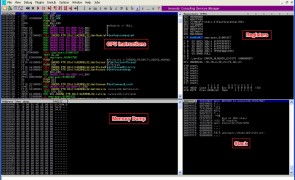
Overview Welcome to Part 1 of a series of posts on Windows Exploit Development. In this first installment I’ll cover just the basics necessary to understand the content of future posts, including some Assembly syntax, Windows memory layout, and using a debugger. This will not be a comprehensive discussion on any of these topics so if you have no exposure to Assembly or if anything is unclear after you read…
Read more... Security Sift
Security Sift
are closed