When is Clickjacking NOT a concern?
According to Microsoft, when it involves more than 1 click. That’s the feedback I received when I recently submitted a Clickjacking bug to Microsoft’s Security team. This particular Clickjacking bug, on an authenticated portion of the site, could induce a victim to unknowingly change their account privacy settings. The problem, according to Microsoft, is that it requires a minimum of two clicks; one to change the privacy setting and one…
Read more...Tags:bug bounty , Clickjacking , Microsoft , web security , X-Frame-Options , XFO
Quotes and XSS — Planning Your Escape
are closed
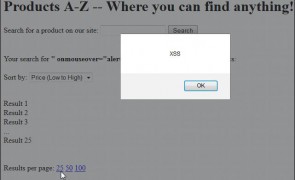
Introduction It’s been my observation that when it comes to XSS prevention, angle brackets associated with HTML and script tags (<>) often get the majority of the attention. While eliminating script tags as a potential XSS vector is a great start, just as important, and seemingly most forgotten when it comes to input validation and output encoding, are double (“) and single (‘) quotes. Whether they are completely ignored or…
Read more...Tags:Cross Site Scripting , encoding , escaping , filter evasion , input validation , penetration testing , quotes , reflected xss , security , web application , web security , XSS
Cross Origin Request Forgery – Attacking HTTPS via HTTP MiTM Injection
are closed
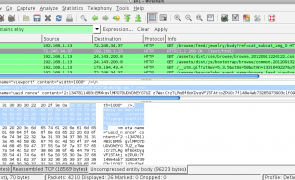
Introduction There are several scenarios in which a web application may choose to deliver both HTTP and HTTPS content. It may employ per-page mixed content, it may use HTTP pre-auth and switch to HTTPS post-auth, or it may continually switch back and forth between HTTP and HTTPS depending on the sensitivity or criticality of the functions being performed by the user (i.e. browsing media content vs. making online purchases). For…
Read more...Tags:csrf , http injection , mitm , request forgery , session management , web security
XSS with a little help from ASP.NET and IE9
are closed
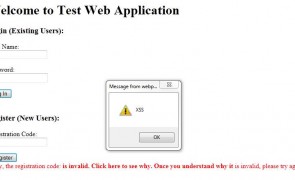
Here I’ll demonstrate how it’s possible to evade ASP .NET Request Validation and take advantage of Internet Explorer 9 quirks to execute a working XSS exploit. Let’s look at a scenario… You suspect an ASP.NET application you’re testing is vulnerable to reflected XSS because it displays user input to the screen. Its login page includes a registration function and if a user inputs the wrong registration number (passed via a…
Read more...Tags:ASP , ASP.NET , Cross Site Scripting , IE9 , Internet Explorer , web security , XSS
 Security Sift
Security Sift
are closed