Testing Optionsbleed
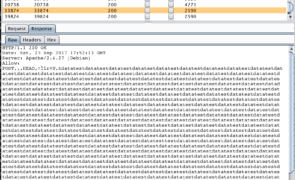
Introduction I took a few minutes to test the Optionsbleed vuln (CVE-2017-9798), specifically to see whether modifying the length and/or quantity of Options/Methods in the .htaccess file would enable me to extract anything of substance from memory. Ultimately it seems that by modifying the length of the entries in the .htaccess file, I was able to gain access to hundreds of bytes of POST data of a different virtual host. Note: Since originally…
Read more...Tags:apache , CVE-2017-9798 , exploit , htaccess , Optionsbleed , vulnerability
Phishing for Shellshock
are closed
Introduction I thought I was done writing about Shellshock, but a recent discussion with some colleagues got me back on the topic. We were commenting about how organizations tend to react very quickly to patching external assets for a bug like Shellshock but many probably wait to patch internal assets due to a false sense of security. It got me thinking about how an external actor could exploit a bug like…
Read more...Tags:exploit , JavaScript , phishing , scan , shell , shellshock , shock , vulnerability
 Security Sift
Security Sift
are closed