peCloak.py – An Experiment in AV Evasion
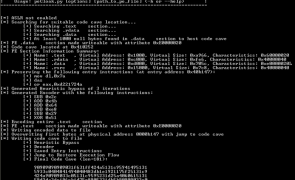
Introduction I just wrapped up the Offensive Security Cracking The Perimeter (CTP) course and one of the topics was AV evasion. Although I write a lot of custom scripts and tools, when it comes to AV evasion, I typically rely on the tools and methods of others (Veil, powershell, python, custom shellcode). That said, the great thing about courses like CTP is they give me an excuse to investigate a topic that I haven’t…
Read more...Tags:anti-virus , antivirus , av , av evasion , Avast , AVG , Avira , Bitdefender , BullGuard , code cave , Comodo , detection , ESET , evasion , heuristics , Kaspersky , malware , Malwarebytes , McAfee , metasploit , Microsoft , Panda , peCloak , pefile , pydasm , python , SectionDoubleP , Spybot , symantec , Trend Micro , virus
Fun With Teensy
are closed

Introduction I’ve been wanting to write about the Teensy and its application in security testing or some time now. It’s extremely useful for executing scripts on a target machine without the need for human-to-keyboard interaction. It can be used to bypass auto-run, AV scanning, and encryption policies commonly targeting removable media devices in an enterprise environment. I’ve used it in my security testing to run recon/enumeration scripts, execute reverse shells, exploit local…
Read more...Tags:av bypass , dip switch , exploit , linux , mac , Microsoft , Offsec , penetration testing , pentesting , reverse shell , symantec , teensy , windows
 Security Sift
Security Sift
are closed