Offensive Security’s CTP and OSCE – My Experience
Overview I had been wanting to take the Cracking The Perimeter (CTP) course for some time but my schedule was pretty hectic. I finally forced myself to start it at the beginning of the new year and I’m really glad I did. As promised, here is my review… Prerequisites Offsec states the following: Many pre-requisites are required, such as good familiarity with a Ollydbg, and a general mastery of offensive network security techniques. Definitely sound advice….
Read more...Tags:certification , cracking the perimeter , ctp , Kali , Offensive Security , Offsec , osce , OSCP , penetration testing , security
Passive Reconnaissance
are closed
Introduction Recently, while watching the House Committee hearings on the security of Healthcare.gov, I was disappointed to hear testimony likening passive reconnaissance to a form of unauthorized/illegal activity that involved potentially invasive actions such as port/vulnerability scanning. To the contrary, passive recon can be one of the most useful and unobtrusive methods of data gathering for any penetration test or security assessment. In this post I outline what passive reconnaissance…
Read more...Tags:advanced search , burp , burpsuite , exploit-db , ghdb , google , google hacking , healthcare.gov , maltego , nerdydata , passive , passive recon , passive reconnaissance , pastebin , recon , reconnaissance , security , shodan
Securing Healthcare.gov – Failures, Fixes, and Next Steps
are closed

Introduction The views expressed in this blog are my own. Just to be clear, that means they are not the views of my employer, co-workers, family, friends, casual acquaintances, strangers, or anyone other than myself. There has been plenty of news coverage about the security flaws that have plagued Healthcare.gov since it went live in October 2013: Hackers: HealthCare.gov still riddled with potential security issues Exclusive: Security Risks Seen at…
Read more...Tags:Air Force , C&A , Certification and Accreditation , CMS , dave kennedy , Frank Baitman , healthcare , healthcare.gov , HHS , Kevin Charest , Larry Ponemon , Lunarline , obamacare , ponemon , security , Superior Solutions , Teresa Fryer , TrustedSec , Waylon Krush
Quotes and XSS — Planning Your Escape
are closed
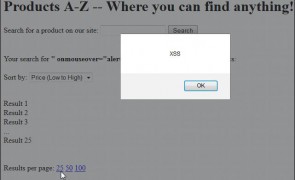
Introduction It’s been my observation that when it comes to XSS prevention, angle brackets associated with HTML and script tags (<>) often get the majority of the attention. While eliminating script tags as a potential XSS vector is a great start, just as important, and seemingly most forgotten when it comes to input validation and output encoding, are double (“) and single (‘) quotes. Whether they are completely ignored or…
Read more...Tags:Cross Site Scripting , encoding , escaping , filter evasion , input validation , penetration testing , quotes , reflected xss , security , web application , web security , XSS
Not your breach, but still your concern
are closed

Why your organization should be concerned with others’ breaches. It seems we’re constantly reading about breaches that result in the leak of login credentials–Gawker, Toshiba, Sony, Yahoo, LinkedIn…this list goes on. Just this week ArenaNet (developers for Guild Wars 2) announced they are experiencing account hacks believed to be facilitated by the use of password lists stolen from other games and sites. Many organizational executives or security personnel might read about these…
Read more... Security Sift
Security Sift
are closed