Abusing Microsoft Office DDE
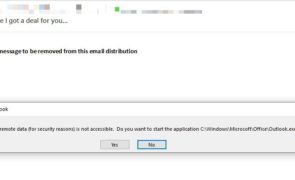
Introduction Earlier this month I came across a post by the team at SensePost outlining their macro-less code execution technique using the antiquated DDE feature of Microsoft Word. As you may be aware, this feature has existed in Office for many years and was even written about over 15 years ago as a potential threat vector. Old or not, as we continue to put up obstacles in front of malicious actors…
Read more...Tags:dde , ddeauto , dynamic data exchange , Microsoft , Microsoft Word , office , outlook , phishing , word
Phishing with Macros and Powershell
are closed
Over the past 6 months, it seems we’ve been experiencing a resurgence of macro-based malware, possibly because it’s such a simple and proven means of delivering a phishing payload to large organizations. If you’re performing a penetration test against an organization and you have reason to believe untrusted macro execution is enabled, they can also be a good means to test user awareness and gain a foothold via social engineering. Regardless of their popularity,…
Read more...Tags:email , exchange , exploit , macro , Microsoft , microsoft office , office , phishing , powershell
An Analysis Of MS15-034
are closed
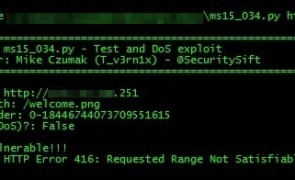
Introduction By now you’ve undoubtedly heard about MS15-034. The following is a collection of my cursory research and thoughts on this vulnerability. In addition, here is a small list of related resources, some of which I also reference in the sections that follow: Microsoft Security Bulletin MS15-034 (Microsoft) The Delicate Art of Remote Checks – A Glance Into MS15-034 (Beyond Trust) MS15-034: HTTP.sys (IIS) DoS And Possible Remote Code Execution. PATCH…
Read more...Tags:http , http.sys , ms15_034 , ms15-034 , phishing , python , range , range header , rce , remote code execution , shellshock
Phishing for Shellshock
are closed
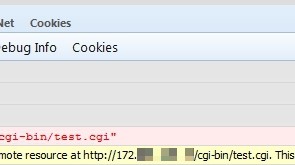
Introduction I thought I was done writing about Shellshock, but a recent discussion with some colleagues got me back on the topic. We were commenting about how organizations tend to react very quickly to patching external assets for a bug like Shellshock but many probably wait to patch internal assets due to a false sense of security. It got me thinking about how an external actor could exploit a bug like…
Read more...Tags:exploit , JavaScript , phishing , scan , shell , shellshock , shock , vulnerability
Why Google Makes My Job More Difficult
are closed
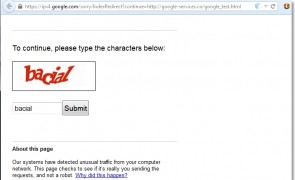
Let me start this post by saying I’m a huge Google fan. I use multiple Android devices and like many others, I’ve become an avid user of services such as Gmail, Docs, Maps, Photos, and Youtube. I even find myself fondly reminiscing about discontinued services such as Reader. And, if you’re like me, Google search has become an instrumental tool in your professional endeavors. So please keep in mind, this post is…
Read more...Tags:docs , google , google docs , phishing , redirection , redirector , redirects , unvalidated redirects
 Security Sift
Security Sift
are closed