Developing a Security Assessment Program
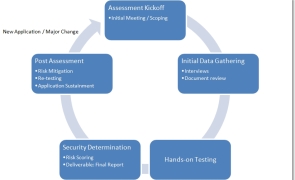
Introduction Most organizations and are deploying new applications and technologies at a high rate and without a means to adequately assess them prior to implementation, it’s difficult to accurately gauge your organization’s risk. No matter what the size or industry, it’s imperative that an organization has a standardized and repeatable process for assessing the security of the IT solutions it implements. My goal with today’s post is to provide some recommendations on…
Read more...Tags:application security , assessment , nist , penetration testing , pentesting , risk , risk management
Fun With Teensy
are closed

Introduction I’ve been wanting to write about the Teensy and its application in security testing or some time now. It’s extremely useful for executing scripts on a target machine without the need for human-to-keyboard interaction. It can be used to bypass auto-run, AV scanning, and encryption policies commonly targeting removable media devices in an enterprise environment. I’ve used it in my security testing to run recon/enumeration scripts, execute reverse shells, exploit local…
Read more...Tags:av bypass , dip switch , exploit , linux , mac , Microsoft , Offsec , penetration testing , pentesting , reverse shell , symantec , teensy , windows
 Security Sift
Security Sift
are closed