Passive Reconnaissance
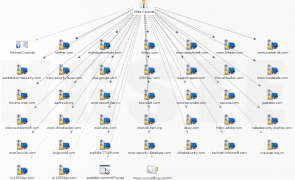
Introduction Recently, while watching the House Committee hearings on the security of Healthcare.gov, I was disappointed to hear testimony likening passive reconnaissance to a form of unauthorized/illegal activity that involved potentially invasive actions such as port/vulnerability scanning. To the contrary, passive recon can be one of the most useful and unobtrusive methods of data gathering for any penetration test or security assessment. In this post I outline what passive reconnaissance…
Read more...Tags:advanced search , burp , burpsuite , exploit-db , ghdb , google , google hacking , healthcare.gov , maltego , nerdydata , passive , passive recon , passive reconnaissance , pastebin , recon , reconnaissance , security , shodan
Not your breach, but still your concern
are closed

Why your organization should be concerned with others’ breaches. It seems we’re constantly reading about breaches that result in the leak of login credentials–Gawker, Toshiba, Sony, Yahoo, LinkedIn…this list goes on. Just this week ArenaNet (developers for Guild Wars 2) announced they are experiencing account hacks believed to be facilitated by the use of password lists stolen from other games and sites. Many organizational executives or security personnel might read about these…
Read more... Security Sift
Security Sift
are closed