Understanding WordPress Auth Cookies
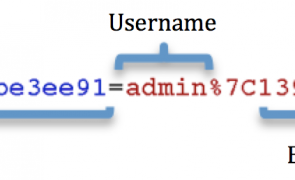
Introduction A recently published vulnerability prompted me to take another look at the wp_validate_auth_cookie WordPress function which is responsible for validating authenticated user requests and ultimately controls access to to your WordPress installation. This post is not about that specific vulnerability (more info here) but rather about how WordPress generates and validates authentication cookies to authorize user requests. If you’re a WordPress user, I encourage you to read on to see what stands between malicious actors and…
Read more...Tags:authentication , brute force , cookie , hash , key , password , salt , secret , wordpress , wp_validate_auth_cookie
Not your breach, but still your concern
are closed

Why your organization should be concerned with others’ breaches. It seems we’re constantly reading about breaches that result in the leak of login credentials–Gawker, Toshiba, Sony, Yahoo, LinkedIn…this list goes on. Just this week ArenaNet (developers for Guild Wars 2) announced they are experiencing account hacks believed to be facilitated by the use of password lists stolen from other games and sites. Many organizational executives or security personnel might read about these…
Read more... Security Sift
Security Sift
are closed