Windows Exploit Development – Part 6: SEH Exploits
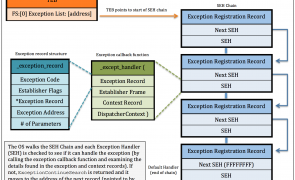
Introduction The buffer overflow exploits covered so far in this tutorial series have generally involved some form of direct EIP overwrite using a CALL or JMP instruction(s) to reach our shellcode. Today we’ll take a look at a different approach using Windows Structured Exception Handling (SEH). Before I begin explaining the basic mechanics of Windows Structured Exception Handling (as it’s implemented in an x86, 32-bit environment) it bears mentioning that…
Read more...Windows Exploit Development – Part 2: Intro to Stack Based Overflows
are closed
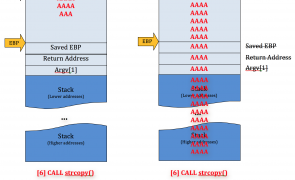
Overview Welcome to Part 2 of my Windows Exploit Development series. In the first post, I covered some basic concepts that should be considered pre-requisites for continuing with Part 2 and beyond. If you haven’t done so, I recommend at least taking a cursory look at the first post to ensure you’ve got a firm grasp on all of the concepts presented. Building on that knowledge, I now want to…
Read more...Tags:ASX To MP3 Converter , buffer overflow , debugger , exploit , immunity , mona , mona plugin , overflow , shellcode , stack based buffer overflow , stack based overflow , stack overflow
 Security Sift
Security Sift
are closed