Abusing Microsoft Office DDE
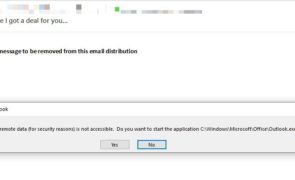
Introduction Earlier this month I came across a post by the team at SensePost outlining their macro-less code execution technique using the antiquated DDE feature of Microsoft Word. As you may be aware, this feature has existed in Office for many years and was even written about over 15 years ago as a potential threat vector. Old or not, as we continue to put up obstacles in front of malicious actors…
Read more...Tags:dde , ddeauto , dynamic data exchange , Microsoft , Microsoft Word , office , outlook , phishing , word
Phishing with Macros and Powershell
are closed
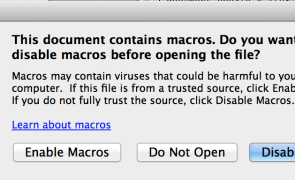
Over the past 6 months, it seems we’ve been experiencing a resurgence of macro-based malware, possibly because it’s such a simple and proven means of delivering a phishing payload to large organizations. If you’re performing a penetration test against an organization and you have reason to believe untrusted macro execution is enabled, they can also be a good means to test user awareness and gain a foothold via social engineering. Regardless of their popularity,…
Read more...Tags:email , exchange , exploit , macro , Microsoft , microsoft office , office , phishing , powershell
peCloak.py – An Experiment in AV Evasion
are closed
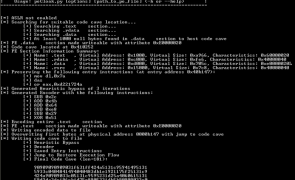
Introduction I just wrapped up the Offensive Security Cracking The Perimeter (CTP) course and one of the topics was AV evasion. Although I write a lot of custom scripts and tools, when it comes to AV evasion, I typically rely on the tools and methods of others (Veil, powershell, python, custom shellcode). That said, the great thing about courses like CTP is they give me an excuse to investigate a topic that I haven’t…
Read more...Tags:anti-virus , antivirus , av , av evasion , Avast , AVG , Avira , Bitdefender , BullGuard , code cave , Comodo , detection , ESET , evasion , heuristics , Kaspersky , malware , Malwarebytes , McAfee , metasploit , Microsoft , Panda , peCloak , pefile , pydasm , python , SectionDoubleP , Spybot , symantec , Trend Micro , virus
Windows Exploit Development – Part 7: Unicode Buffer Overflows
are closed
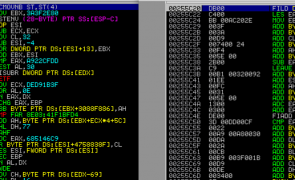
Introduction In this seventh installment of the Windows Exploit Development Series, I’ll introduce Unicode Buffer Overflows. We’ll start with a brief introduction to Unicode (what it is and why/how it’s used in Windows) and then jump right in to some example exploits. If you plan on following along, I recommend you have the following: A Windows environment (XP or Win 7 — my demos will be on the latter) Metasploit, Alpha2 or…
Read more...Tags:allplayer , alpha2 , alpha3 , ansi , ascii , bladeapimonitor , buffer overflow , debugger , dumpbin , exploit , immunity , Microsoft , perl , seh , shellcode , structured exception handler , structured exception handling , unicode , utf-16 , utf-8 , venetian , venetian shellcode , win32 , windows
Fun With Teensy
are closed

Introduction I’ve been wanting to write about the Teensy and its application in security testing or some time now. It’s extremely useful for executing scripts on a target machine without the need for human-to-keyboard interaction. It can be used to bypass auto-run, AV scanning, and encryption policies commonly targeting removable media devices in an enterprise environment. I’ve used it in my security testing to run recon/enumeration scripts, execute reverse shells, exploit local…
Read more...Tags:av bypass , dip switch , exploit , linux , mac , Microsoft , Offsec , penetration testing , pentesting , reverse shell , symantec , teensy , windows
When is Clickjacking NOT a concern?
are closed
According to Microsoft, when it involves more than 1 click. That’s the feedback I received when I recently submitted a Clickjacking bug to Microsoft’s Security team. This particular Clickjacking bug, on an authenticated portion of the site, could induce a victim to unknowingly change their account privacy settings. The problem, according to Microsoft, is that it requires a minimum of two clicks; one to change the privacy setting and one…
Read more...Tags:bug bounty , Clickjacking , Microsoft , web security , X-Frame-Options , XFO
 Security Sift
Security Sift
are closed