peCloak.py – An Experiment in AV Evasion
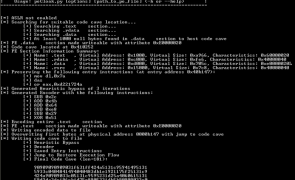
Introduction I just wrapped up the Offensive Security Cracking The Perimeter (CTP) course and one of the topics was AV evasion. Although I write a lot of custom scripts and tools, when it comes to AV evasion, I typically rely on the tools and methods of others (Veil, powershell, python, custom shellcode). That said, the great thing about courses like CTP is they give me an excuse to investigate a topic that I haven’t…
Read more...Tags:anti-virus , antivirus , av , av evasion , Avast , AVG , Avira , Bitdefender , BullGuard , code cave , Comodo , detection , ESET , evasion , heuristics , Kaspersky , malware , Malwarebytes , McAfee , metasploit , Microsoft , Panda , peCloak , pefile , pydasm , python , SectionDoubleP , Spybot , symantec , Trend Micro , virus
Windows Exploit Development – Part 4: Locating Shellcode With Jumps
are closed
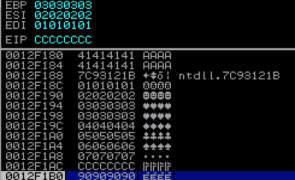
Overview In Parts 2 and 3, we built and improved upon an exploit for ASX To MP3 converter. Even though it had it’s flaws, as far as exploits go, it was pretty straightforward — direct EIP overwrite with a jump directly to a register that pointed to our shellcode. Things aren’t always that easy. Quite often you have to do a bit more work to get the application to execute…
Read more... Security Sift
Security Sift
are closed