Windows Exploit Development – Part 7: Unicode Buffer Overflows
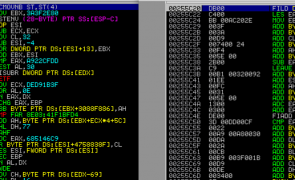
Introduction In this seventh installment of the Windows Exploit Development Series, I’ll introduce Unicode Buffer Overflows. We’ll start with a brief introduction to Unicode (what it is and why/how it’s used in Windows) and then jump right in to some example exploits. If you plan on following along, I recommend you have the following: A Windows environment (XP or Win 7 — my demos will be on the latter) Metasploit, Alpha2 or…
Read more...Tags:allplayer , alpha2 , alpha3 , ansi , ascii , bladeapimonitor , buffer overflow , debugger , dumpbin , exploit , immunity , Microsoft , perl , seh , shellcode , structured exception handler , structured exception handling , unicode , utf-16 , utf-8 , venetian , venetian shellcode , win32 , windows
Windows Exploit Development – Part 6: SEH Exploits
are closed
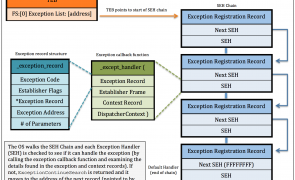
Introduction The buffer overflow exploits covered so far in this tutorial series have generally involved some form of direct EIP overwrite using a CALL or JMP instruction(s) to reach our shellcode. Today we’ll take a look at a different approach using Windows Structured Exception Handling (SEH). Before I begin explaining the basic mechanics of Windows Structured Exception Handling (as it’s implemented in an x86, 32-bit environment) it bears mentioning that…
Read more...Windows Exploit Development – Part 4: Locating Shellcode With Jumps
are closed
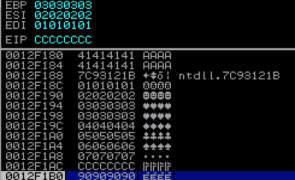
Overview In Parts 2 and 3, we built and improved upon an exploit for ASX To MP3 converter. Even though it had it’s flaws, as far as exploits go, it was pretty straightforward — direct EIP overwrite with a jump directly to a register that pointed to our shellcode. Things aren’t always that easy. Quite often you have to do a bit more work to get the application to execute…
Read more...Windows Exploit Development – Part 3: Changing Offsets and Rebased Modules
are closed

Overview In Part 2 we constructed a basic stack based overflow exploit for ASX To MP3 Converter. As I indicated in that post, the exploit itself is far from perfect. Successful EIP overwrite is influenced by the file path of the m3u file. In addition, although application modules are preferred when selecting jump/call addresses, the application DLL we used was rebased, meaning the address to our CALL EBX instruction is…
Read more...Windows Exploit Development – Part 2: Intro to Stack Based Overflows
are closed
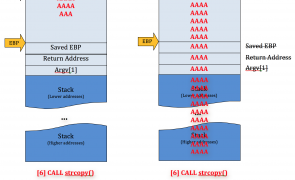
Overview Welcome to Part 2 of my Windows Exploit Development series. In the first post, I covered some basic concepts that should be considered pre-requisites for continuing with Part 2 and beyond. If you haven’t done so, I recommend at least taking a cursory look at the first post to ensure you’ve got a firm grasp on all of the concepts presented. Building on that knowledge, I now want to…
Read more...Tags:ASX To MP3 Converter , buffer overflow , debugger , exploit , immunity , mona , mona plugin , overflow , shellcode , stack based buffer overflow , stack based overflow , stack overflow
Windows Exploit Development – Part 1: The Basics
are closed
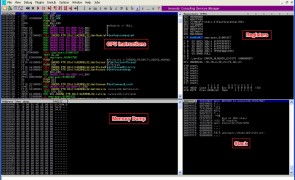
Overview Welcome to Part 1 of a series of posts on Windows Exploit Development. In this first installment I’ll cover just the basics necessary to understand the content of future posts, including some Assembly syntax, Windows memory layout, and using a debugger. This will not be a comprehensive discussion on any of these topics so if you have no exposure to Assembly or if anything is unclear after you read…
Read more... Security Sift
Security Sift
are closed