Passive Reconnaissance
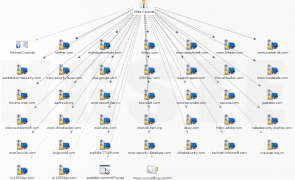
Introduction Recently, while watching the House Committee hearings on the security of Healthcare.gov, I was disappointed to hear testimony likening passive reconnaissance to a form of unauthorized/illegal activity that involved potentially invasive actions such as port/vulnerability scanning. To the contrary, passive recon can be one of the most useful and unobtrusive methods of data gathering for any penetration test or security assessment. In this post I outline what passive reconnaissance…
Read more...Tags:advanced search , burp , burpsuite , exploit-db , ghdb , google , google hacking , healthcare.gov , maltego , nerdydata , passive , passive recon , passive reconnaissance , pastebin , recon , reconnaissance , security , shodan
Securing Healthcare.gov – Failures, Fixes, and Next Steps
are closed

Introduction The views expressed in this blog are my own. Just to be clear, that means they are not the views of my employer, co-workers, family, friends, casual acquaintances, strangers, or anyone other than myself. There has been plenty of news coverage about the security flaws that have plagued Healthcare.gov since it went live in October 2013: Hackers: HealthCare.gov still riddled with potential security issues Exclusive: Security Risks Seen at…
Read more...Tags:Air Force , C&A , Certification and Accreditation , CMS , dave kennedy , Frank Baitman , healthcare , healthcare.gov , HHS , Kevin Charest , Larry Ponemon , Lunarline , obamacare , ponemon , security , Superior Solutions , Teresa Fryer , TrustedSec , Waylon Krush
 Security Sift
Security Sift
are closed