11 Fallacies of Web Application Security

Introduction By far, application security testing is one of the best parts of my job. Working one-on-one with application developers, I find that nearly all want to do the right thing when it comes to security but many face common misconceptions about security vulnerabilities (and the necessary remediation actions). This is my attempt to address some of those misconceptions surrounding authentication, session management, access control, SQL Injection, XSS, and CSRF…
Read more...Tags:authentication , csrf , injection , session management , web application security , XSS
Cross Origin Request Forgery Pt 2 – Exploiting Browser Security
are closed
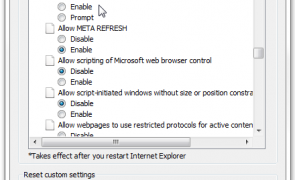
Introduction In my previous post I demonstrated how insecure handling of CSRF tokens by applications that switch between HTTP and HTTPS can put users at risk of request forgery attacks via man-in-the-middle interception. Today I ‘ll expand upon this point and demonstrate how it can provide remote attackers the same opportunity, if the user’s browser is not configured to prevent insecure cross-domain communications. Recall in the last post, the site…
Read more...Tags:browser security , cross domain , cross origin , cross site request forgery , csrf
Cross Origin Request Forgery – Attacking HTTPS via HTTP MiTM Injection
are closed
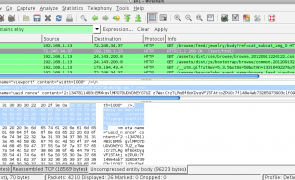
Introduction There are several scenarios in which a web application may choose to deliver both HTTP and HTTPS content. It may employ per-page mixed content, it may use HTTP pre-auth and switch to HTTPS post-auth, or it may continually switch back and forth between HTTP and HTTPS depending on the sensitivity or criticality of the functions being performed by the user (i.e. browsing media content vs. making online purchases). For…
Read more...Tags:csrf , http injection , mitm , request forgery , session management , web security
 Security Sift
Security Sift
are closed