How NOT To Restrict Cross-Domain Flash Content
Introduction Insufficient input validation is a problem I encounter practically every time I test an application. I’ve talked about relying on input validation as a prevention mechanism before (see here and item #8 here) but since it’s such a prevalent problem I figured I’d take the time to write about it once again. While a good supplemental control, by itself input validation is usually woefully inadequate. Quite frankly, it often requires much…
Read more...Tags:bounty , bug bounty , cross domain , crossdomain , flash , jpexs , paypal
Who do you trust? Cross-domain content extraction with Clickjacking
are closed

Overview Today I’ll illustrate how it’s possible to extract sensitive data via Clickjacking by taking advantage of some liberal framing behaviors in Firefox coupled with a X-Frame-Options:Allow header that forms an implicit trust relationship between two sites. This Clickjacking POC takes advantage of several site and browser behaviors including: Etsy.com set an X-Frames-Options: Allow header when accessed directly from a search engine query result Microsoft Bing search engine allows framing…
Read more...Tags:Bing , Clickjacking , content extraction , cross domain , Etsy , Firefox , trust , X-Frame-Options
Cross Origin Request Forgery Pt 2 – Exploiting Browser Security
are closed
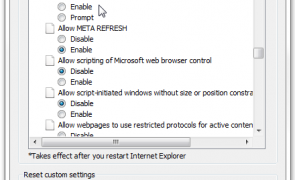
Introduction In my previous post I demonstrated how insecure handling of CSRF tokens by applications that switch between HTTP and HTTPS can put users at risk of request forgery attacks via man-in-the-middle interception. Today I ‘ll expand upon this point and demonstrate how it can provide remote attackers the same opportunity, if the user’s browser is not configured to prevent insecure cross-domain communications. Recall in the last post, the site…
Read more...Tags:browser security , cross domain , cross origin , cross site request forgery , csrf
 Security Sift
Security Sift
are closed