Google
Current tag: buffer
Windows Exploit Development – Part 6: SEH Exploits
Written on:March 25, 2014
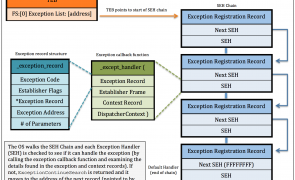
Introduction The buffer overflow exploits covered so far in this tutorial series have generally involved some form of direct EIP overwrite using a CALL or JMP instruction(s) to reach our shellcode. Today we’ll take a look at a different approach using Windows Structured Exception Handling (SEH). Before I begin explaining the basic mechanics of Windows Structured Exception Handling (as it’s implemented in an x86, 32-bit environment) it bears mentioning that…
Read more... Security Sift
Security Sift
are closed