Understanding WordPress Auth Cookies
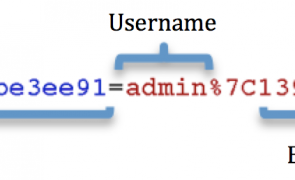
Introduction A recently published vulnerability prompted me to take another look at the wp_validate_auth_cookie WordPress function which is responsible for validating authenticated user requests and ultimately controls access to to your WordPress installation. This post is not about that specific vulnerability (more info here) but rather about how WordPress generates and validates authentication cookies to authorize user requests. If you’re a WordPress user, I encourage you to read on to see what stands between malicious actors and…
Read more...Tags:authentication , brute force , cookie , hash , key , password , salt , secret , wordpress , wp_validate_auth_cookie
11 Fallacies of Web Application Security
are closed

Introduction By far, application security testing is one of the best parts of my job. Working one-on-one with application developers, I find that nearly all want to do the right thing when it comes to security but many face common misconceptions about security vulnerabilities (and the necessary remediation actions). This is my attempt to address some of those misconceptions surrounding authentication, session management, access control, SQL Injection, XSS, and CSRF…
Read more...Tags:authentication , csrf , injection , session management , web application security , XSS
 Security Sift
Security Sift
are closed