Intro
Each year the Verizon RISK Team releases its highly anticipated Data Breach Investigations Report (DBIR) — download this year’s report here. For some of us, equally as exciting as the content of the report is the DBIR Cover Challenge — a multi-stage puzzle that requires participants to follow obscure (and often hilarious) clues, testing their critical thinking and problem solving skills along the way. Following two consecutive fourth place finishes, we were determined to take home a victory this year.
This year’s win was a team effort with my InfoSec colleagues Andrij “Andy” Kuzyszyn (@Blackjack988) and William “Bill” Pustorino (@laughingwill). Some might say that undertaking the challenge as a group provides an advantage. While it certainly does have its upsides (including serving as a great team-building and problem solving exercise), it also resulted in three over-analyzing minds dreaming up wild ideas that would ultimately lead to false starts, hours of stagnation, and an unhealthy fixation on one particular RISK Team member.
The following post covers two days of (many) miscues and (far fewer) breakthroughs that eventually led to becoming the first participants to solve this year’s puzzle.
Day 1 – Release, Renew…cannot find the file specified.
This year’s challenge got off to a false start as the first release of the report did not include all of the clues and it was temporarily put on hold. This actually gave me time to read the content of the report, something I don’t usually don’t get to do until after completing the puzzle. The Verizon team quickly fixed the problem and within a few hours, a renewed version of the report was posted.
Since this is known as the “Cover Challenge”, the first step is inspecting the front and back covers of the report for both visual and hidden clues. We found hidden text in both. The text from the front cover was:
f 3 8 b 8 e 9 2 f 8 1 2 f 9 f 4 f 2 6 b e 4 7 9 3 8 2 7 d 9 0 6
We removed the spaces and concatenated the two lines to get a single 32-character string (f38b8e92f812f9f4f26be4793827d906). At first we assumed it might be a (MD5?) hash but we weren’t yet sure what to do with it. The hidden text from the back cover was a lengthy base64-encoded block (shortened here for formatting purposes).
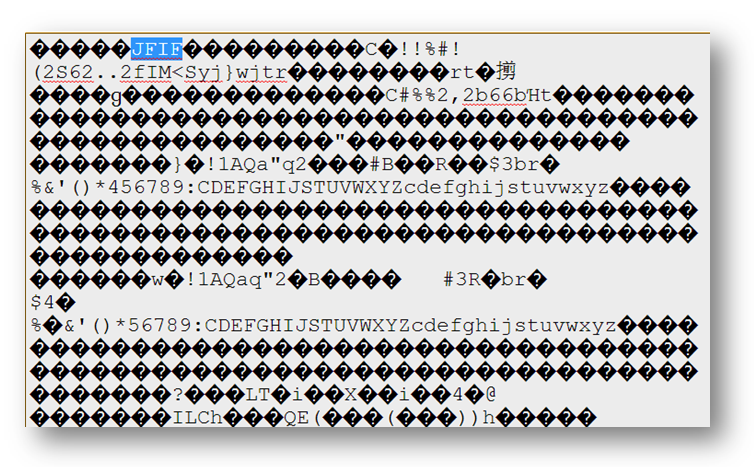
/9j/4AAQSkZJRgABAQAAAQABAAD/2wBDACEXGR0ZFSEdGx0lIyEoMlM2Mi4uMmZJTTxTeWp/fXdqdHKFlr+ihY21kHJ0puOotcbM1tjWgaDr/OnQ+r/S1s7/2wBDASMlJTIsMmI2NmLOiXSJzs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7Ozs7/wAARCAGJAgwDASIAAhEBAxEB/8QAHwAAAQUBAQEBAQEAAAAAAAAAAAECAwQFBgcICQoL/8QAtRAAAgEDAwIEAwUFBAQA … kU37G394VcoouFioLM45bn6Un2RuzCrlFFwKX2R/VaQ20g7D86vUGi4FD7PKP4T+dHlyjs1XqWi4Gf8AvR/fo8yUd2q/SHpTEUfPlH8RpRcyjuD+FWHqtJ1oC4/7XJ/s0v2t+6rVcUlFguWheH+6PzpwvB3X9apmlosO5dF3GeuRThPEf4hVCkNFguaYdD0YH8admspetWoaQFuikXpS0gCilpKACiiigBKKKKAFpKKKADFFAooGGKMUtJQI/9k=
We ran it through a base64 decoder (output as plain text) to inspect the contents and the first thing we noticed was the JFIF file type.
We decoded it again, this time as binary, and saved the file as an image:
For those who don’t know (aka “the lucky ones”), this pic is a combination of two memes — Ermahgerd and the World’s best sign flipper. In “Ermahgerd-speak”, the text of the sign translates to “The RISK team welcomes puzzle contestants”. Past years puzzles have included multiple, hard-to-spot visual clues within photos so we spent some time examining the image, but in the end, the only clue was the GitHub link.
The link took us to the Verizon RISK Team GitHub repository page, home of the VERIS schema (see here for a description of VERIS: http://www.verizonenterprise.com/DBIR/2013/).
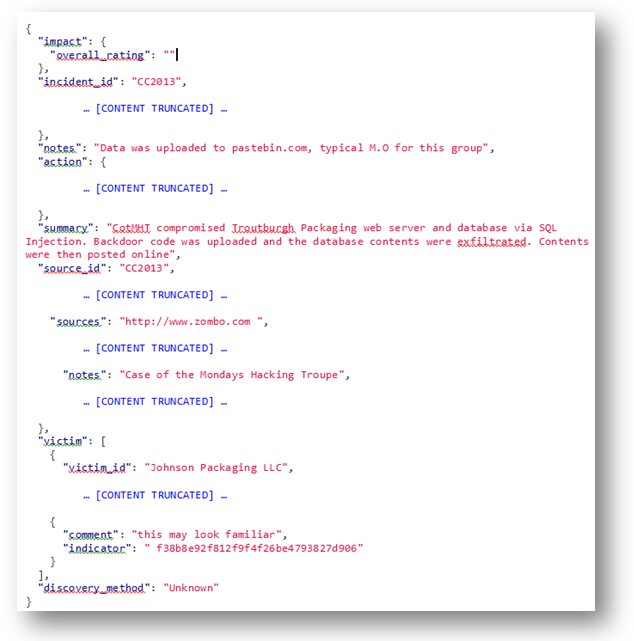
Not really sure where to go from here, we began investigating everything on the site. We started with user profiles, examining all 8 members (and their followers) as well as anyone that “starred” the VERIS repositories (and their followers) to see if any might lead to more clues. While we got unnecessarily familiar with many GitHub members and their respective projects, this ended up leading nowhere and wasted some serious time. We also downloaded both the “veris” and “verisweet” repositories to examine the file content, though they collectively consisted of over 1000 files and we had no idea what we were looking for. After quite some time searching for various key words including “Ermahgerd” and her aliases, “Gersberms” and “Berks”, Andy finally thought to try the 32-character hex string from the front cover and bingo – we got a hit from one of the files in the VERIS repository (osint650.json). The portions of the file we believed to relevant appear below — note the comment/indicator referencing the front cover find from earlier.
One of the first things that caught our eye was the zombo.com link. Surprisingly between the three of us (each of whom spends an unhealthy amount of time in front of the computer surfing the Interwebs), none had ever heard of zombo.com — and thus another wild goose chase ensued. Btw, if you are included in the group of people that have never visited zombo.com, I encourage you to go to the site and listen to the audio—it’s a perfect combination of creepy and fantastic.
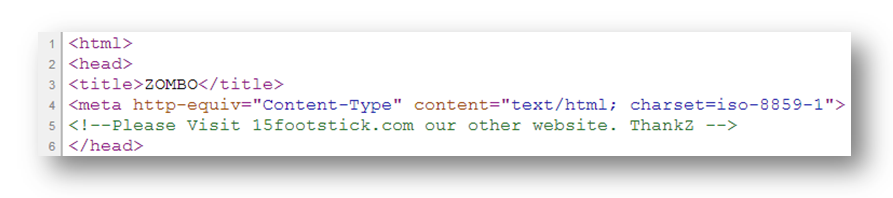
We examined the source of zombo.com and noticed that it referenced 15footstick.com, another peculiar site that we had never heard of.
Despite the fact that nothing on 15footstick.com appeared to have been updated since 2005, I was convinced it was a trick and proceeded to follow every link, watch every video, and inspect the source of every page on the site. Though sometimes entertaining (you must check out the 3-part Independent World Report videos), it was also a complete waste of time and got us no closer to solving the puzzle.
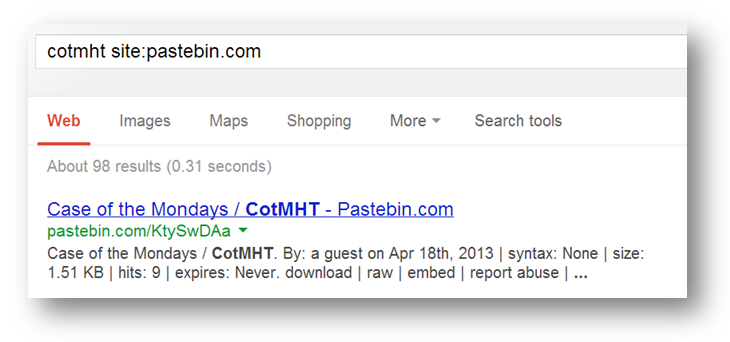
Thankfully, we finally had the sense to “right the ship” and followed the Pastebin reference which led us to the next clue.
From here the first thing we did was crack the password hashes which gave us the following:
Michael Abc Tito Easy Jackie As Jermaine 123 Danzig iiiiiiiiiiiiiiiiiiii
Aside from a clever use of a song lyric, the passwords didn’t appear to give us anything of value. Of course, it did lead to some other (very stupid) questions like: Why was Marlon left off the list? and Why was he replaced by Danzig? While I still demand answers, they clearly had no bearing on the solution of this puzzle so we moved on.
Of course, what we moved on to was yet another dead end — the embedded numbers in the CotMHT block letters at the top of the post. Removing the lines and dollar signs, you’re left with 4 18 9 14 11 13 15 18 5 15 22 1 12 20 9 14 5 . Noting that all of the numbers were less than 26, we converted them to letters and got: DRINK MORE OVALTINE. Again, thinking this could be a clue, we tried some additional searches in the Github repository and wasted more time.
The real clue in the Pastebin post ended up being the reference to the “epic ukulele solo” which thanks to a Google search by Bill, led us to this awesome video on Youtube: https://www.youtube.com/watch?v=M2vRHccdUAg.
One of the first things we noticed was the author of the page — Imstilla Hentz. Since we also participated in last year’s challenge, we recognized this as a reference to “Ima Hintz”, the source of many of the previous puzzle’s clues. Had we thought to investigate this further in this early stage of the challenge, we would have had this thing solved on Day 1 (see the end of this post for an explanation). Of course we were too distracted to think logically and we proceeded to watch the video instead.
While the song in the video — a hilarious DBIR-centric take on the Gotye song “Somebody that I Used to Know” — might be considered an instant classic, the clues needed to solve the puzzle were all on the whiteboard. We quickly got to work trying to decipher each of the items on the board and here’s a synopsis of what we found:
- The coordinates 46°59.91′N 85°06.61′W correspond to the Edmund Fitzgerald wreck site. Of course that meant learning everything there was to know about the ship, including reading the Wikipedia page as well as the (page-turning) 1975 National Transportation Safety Board crash report.
- Soulcrate is a rap trio from the original land of hip hop… Sioux Falls, South Dakota (#sarcasm). The quote “SOULCRATE SUCKA! ALL DAY EVERY DAY.” comes from their song “ALL DAY” — a cool track but another false lead.
- Item number 2 to on the “To Do List” is “Pay Upgrayedd” a reference to the pimp character from the 2006 movie ‘Idiocracy’. I’ve seen the movie once and wasn’t about to watch it again for clues. (If you’re a fan of this movie, I’m sure my colleague @laughingwill would love to discuss).
- The quote about Canada and French fries w/ gravy led to the discovery of a fascinating food called “Poutine” but no further progress in solving the puzzle.
- SETEC Astronomy is an anagram for “Too Many Secrets” and another movie reference (“Sneakers”), but also was not a useful clue.
- The quote “There is still no internationally clear, unified definition of what constitutes a hacking attack” can be attributed to Geng Yansheng, a spokesman for China’s Ministry of National Defense in response to Mandiant’s 2013 report (http://intelreport.mandiant.com/Mandiant_APT1_Report.pdf) outlining hacking activities from a group (the “comment crew”) with ties to China’s military. http://money.cnn.com/2013/02/20/technology/china-cyber-hacking-denial/index.html The Mandiant report is a cool read, but this too led to no further clues.
- We thought #rar ‘thddus might be another anagram or scrambled letters that would lead to a Twitter hash tag search but we couldn’t make anything of it. The Minnesota Vikings helmet also didn’t lead anywhere. Wolfram Alpha gave a quick solution to the derivative problem, but again no clue. We also couldn’t find the origin of the quote on top left (“It’s Ok, Bro I’ve got AV #Truth #NoLie #YOLO”).
- In addition to being a term used to describe a dealer in small goods or men’s clothing, the term Haberdasher also relates to Haberdasher’s Puzzle, a dissection puzzle presented by Henry Dudeney in which a triangle, dissected in four pieces can be rearranged to form a square. A quick visit to the Wikipedia article on Henry Dudeney provided a great motion-based illustration of solving the puzzle. At the time it didn’t mean much, but I was certain it would play a role so I took note.
The real breakthrough clue came from the reference to Colonel J Henry Haberdasher and the letters W O S. Watching the video you’ll notice the W O S changes to HI mom! – W O S + H I = WHOIS
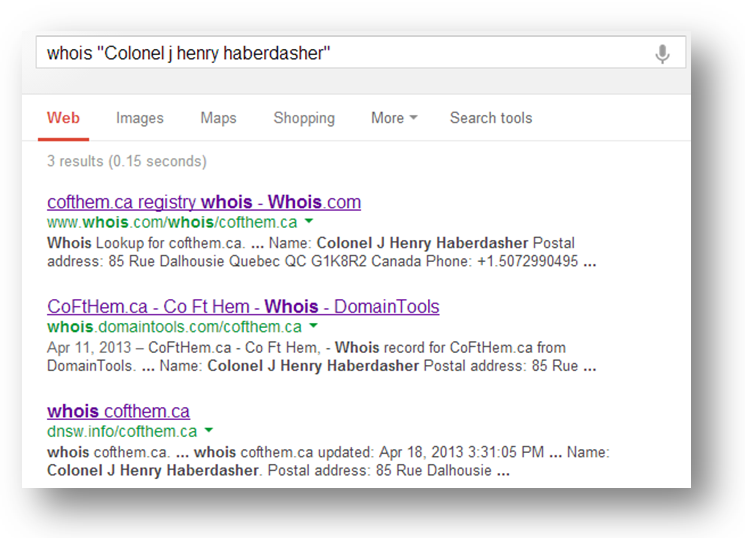
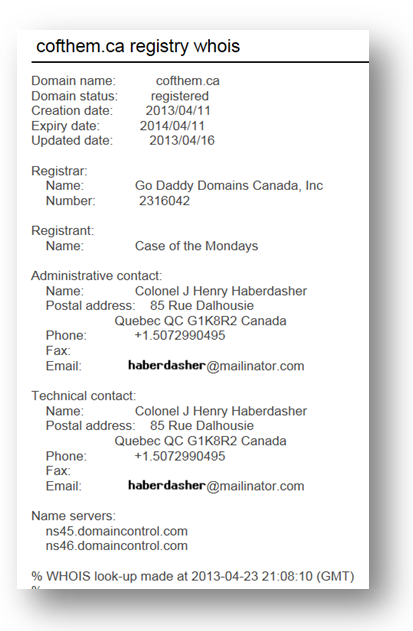
A subsequent Google search led us to the Whois record for cofthem.ca
Cofthem.ca of course is “case of the Mondays” matching both the registrant name and the earlier clue from the Github file. We were convinced the next clue was somewhere in the unique data found in this Whois record: the website, email address, mailing address and phone number.
We started with the website, a Godaddy site with a stock photo background and no content of interest. We examined the source code and did an advanced Google search for the domain but found nothing and moved on to the email address.
Mailinator.com is a disposable email site that creates mailboxes on the fly and allows you to view their contents online. We looked up the haberdasher address but the mailbox was empty. We didn’t want to send a message to the box because we know it would be visible to others and didn’t think a public mailbox would lead to any more clues. We then turned our attention to the phone number.
The area code belongs to Southern Minnesota but further Google searching was fruitless. We called the phone number and got the Google voicemail of Kevin Thompson. We assumed this could be the same Kevin Thompson that serves as the Risk and Intelligence Researcher on the Verizon RISK team, but we held off on leaving a message.
We then researched the mailing address, which corresponded to the Musée de la civilization (Museum of Civilization) located in Quebec City, Canada but after perusing the Wikipedia page for the museum we still had nothing new.
I remembered from my earlier reading that the DBIR (page 36) references social engineering via SMiShing so we took a shot and sent a text message to the phone number we called earlier.
This takes us to the end of the first day of puzzle solving for us. All told, it took us about 4 hours to get this point and it was getting late so we called it a night. This also happens to be where the train completely derails for us and playing as a team leads us further down the rabbit hole than any one person could dream of.
Day 2 – Same old song and (victory) dance
Day two began with a fresh viewing of the video (then another, and another, and…). With no response from our previous night’s text but convinced that the next clue was contained somewhere in this Whois record information, we continued our search.
Unfortunately, I was out of the office and without reliable Internet connection for a good part of the day but I did take with me two screenshots to view on my mobile device – one of the whiteboard from the video and the other of the Whois record. I glanced at the images as often as I could but had no real breakthroughs. Meanwhile the other members of my team were in the office but inundated with work, so progress was slow.
Whenever possible, we would ponder the clues and communicate via email…mostly to consider more dead ends and ask irrelevant questions such as:
Why were the words “Keith”, “WHOIS”, and “Colonel J Henry Haberdasher” all in block lettering and why were the letters COOL in Colonel bolded? Could it be an anagram? (Answer: No)
What happens if you plot Vikings stadium, the Musée de la civilization and the coordinates of the Edmund Fitzgerald wreck on a map? (Answer: nothing)
And then we found it…the Musée de la civilization was also the site of BSides Quebec, a security conference attended by none other than Kevin Thompson (Verizon RISK Team member and owner of the Google voice number). Surely that couldn’t be a coincidence so we absolutely had to find out everything we could about this guy.
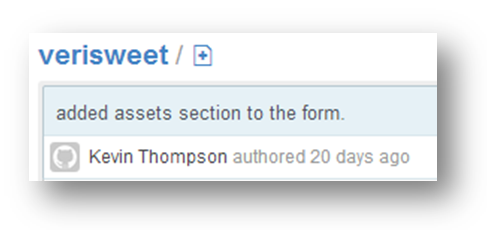
We revisited Github and noticed the verisweet repository was last updated by one Kevin Thompson. That led to a thorough review of that code…which gave us nothing.
We found Kevin Thompson’s LinkedIn profile and noted that his picture matched that of “blackfist” on Github, so those repositories were examined as well (also yielding nothing).
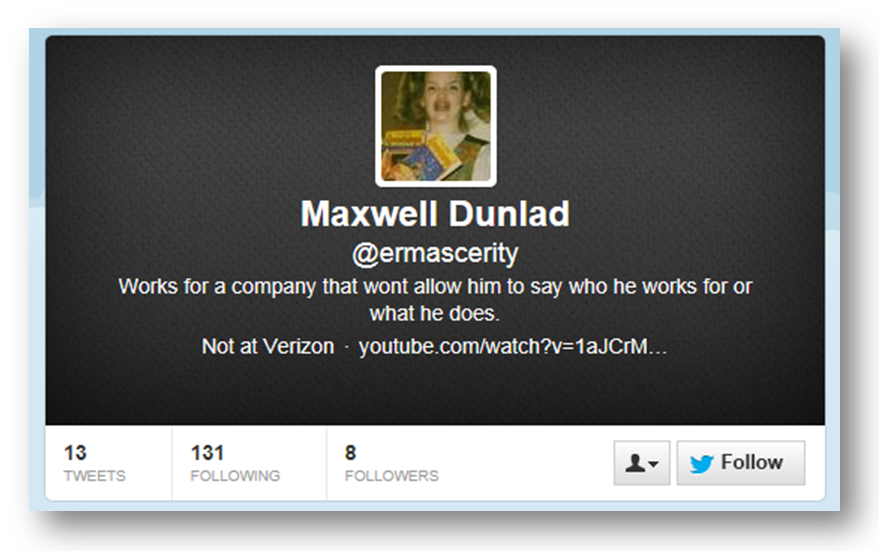
Although we couldn’t find his presentation slides for Quebec, we did find a copy from Bsides Vancouver and wouldn’t you know on slides 6 and 7 we found this:
A twitter search for the hash tag revealed nothing, but a search for the handle @ermascerity led to a profile belonging to Maxwell Dunlad (note the employer “Not at Verizon”).
A Google search for @ermasecurity confirmed our suspicion: Kevin Thompson (ermascerity) on Twitter.
We were confident (#deadwrong) this profile was the clue and proceeded to review the various public tweets and content. Once again, we came up with absolutely nothing.
By this time other participants were quickly catching up. We saw tweets from people viewing the Youtube video and noticed several emails being sent to the habadasher@mailinator.com account. Even though we were certain it would yield no clues, in pure frustration we sent an email of our own. As expected, we received no response.
We did some more Google searches for ermascerity and came across The Digital4ensics Blog, whose author’s name is Keith. We recalled the message on the whiteboard from the Youtube video “Keith: Canada is a country in North America…”.
We then located the associated Github page (note the Verizon RISK Team logo) and proceeded to search the various repositories, with no luck.
We now felt like we were getting nowhere and losing whatever lead we may have had, but resolved to pick up again the next day.
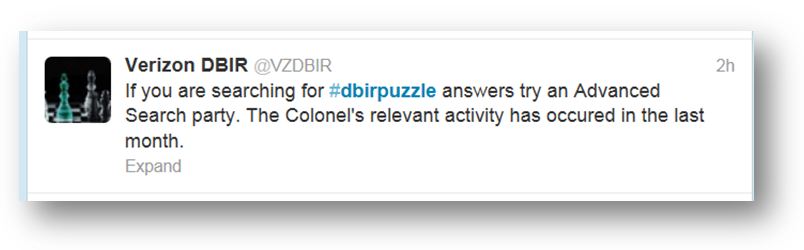
That evening I put the puzzle aside, went to the gym, ate dinner and watched some mindless TV for about an hour. Then, before I went to bed I noticed this tweet that had been sent out from the Verizon DBIR team:
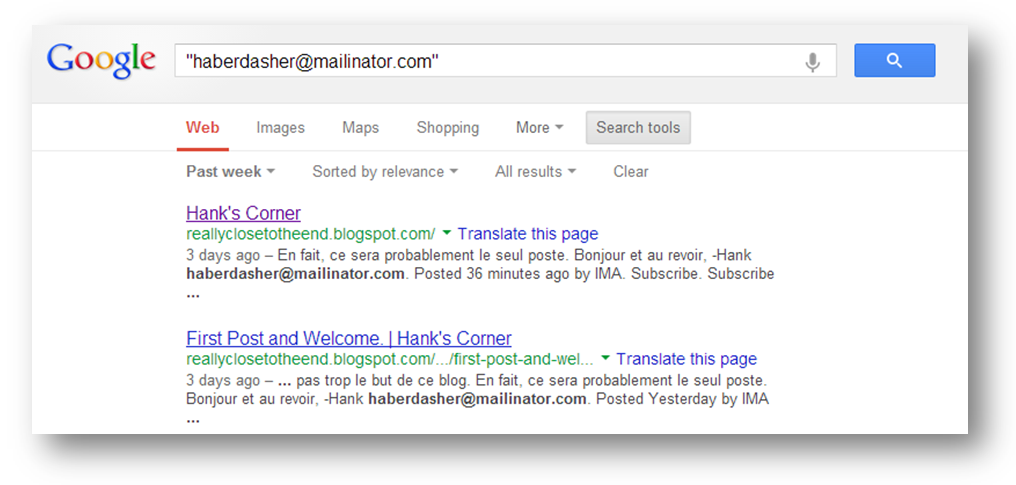
I tried some advanced Google searches for “Colonel J Henry Haberdasher” (and every combination of the name) but found nothing. I then reminded myself that the last verified clue we found was the Whois record and the name was not unique to that clue (it was also in the Youtube video). Surely the info we needed was from the Whois record, leaving the address, phone number, website and email address. We had already established the address belonged to the museum and the phone number and website both seemed to be dead ends. I then did a Google search for haberdasher@mailinator.com, filtering for results in the last week and came up with the following:
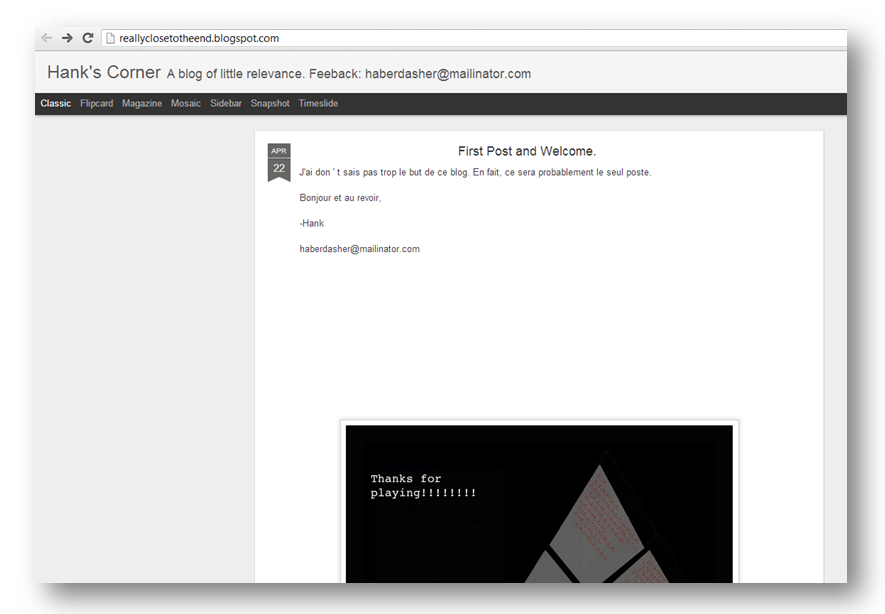
At last!! I sent an email to the team and we got to solving this puzzle. The Google search led to the following blog post:
The text translates to (per Google Translate): “I don’t know too the purpose of this blog. In fact, this will probably be the only post. Hello and goodbye”.
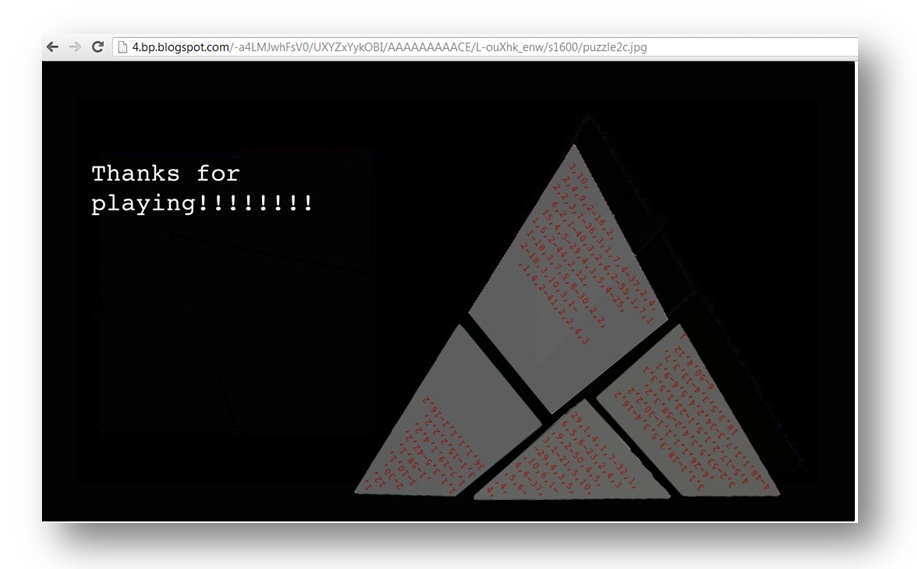
The real clue is in the image further down on the page:
As soon as I saw this, I remembered the Wikipedia post for the haberdasher puzzle. Armed with the knowledge of how to rearrange the pieces to form a square and some rudimentary Photoshop skills, I came up with this:
It was clear that the dashes separated the number sets (42 in all), each of which contained five numbers. In each of the number sets, the first number was the largest. My colleague quickly pointed out the largest number was 48. “Hey wait”, I remembered, “Kevin Thompson’s Bsides presentation had 48 slides”… a thought that I quickly dismissed. It was time to leave that poor guy alone. This did however remind me of the DBIR puzzle from two years ago which used a book cipher (page, paragraph, line, word, character) to construct the winning passphrase from content within the DBIR. It was worth a shot so we opened the report and started mapping number sets to letters.
29,1,4,1,7 e
32,1,3,1,1 m
18,3,5,3,4 a
16,2,6,5,6 i
23,2,4,3,4 l
…
This had to be it! We continued down the number sets until we came up with the winning phrase:
email book cipher again? to dbir@verizon.com
We sent the email as instructed and received a response confirming we were the first to solve the puzzle. Thankfully we didn’t give up that night because just 50 minutes later, previous DBIR cover challenge winner and puzzle whiz David Schuetz (@DarthNull | http://darthnull.org/) took second place. Congrats to him on another great placing!
Solution Summary
Here’s the abridged version of the solution, minus all of the missteps and tangents.
1. Extracted hidden text from front and back covers of the DBIR
2. Decoded base64 from back cover, converted to Ermahgerd image, followed link to Verizon RISK Team’s Github site.
3. Searched VERIS repository on Github for hex string from front cover, discovered json file clue pointing to “CotMHT” Pastebin post.
4. Found Youtube video referenced in the Pastebin post, identified the WHOIS Colonel J. Henry Haberdasher clue
5. Found Whois registry for cofthem.ca (registered to Colonel J. Henry Haberdasher).
6. Performed advanced Google search for haberdasher@mailinator.com (restricted to last 2 weeks) located the “Hank’s Corner” blog post.
7. Rearranged haberdasher puzzle image to reveal the 42 number sets.
8. Constructed winning passphrase “email book cipher again? to dbir@verizon.com” letter-by-letter using “page, paragraph, line, word, character” book cipher.
9. Sent email to Verizon RISK team. And There was Much Rejoicing … Yay!
The day after — High fives and head slaps
The next day as we were re-examining the final clues, we noticed something at the bottom of the Hank’s Corner blog site:
IMA was the same blogger that hosted the previous year’s puzzle clues (IMA HINTZ). Sure enough, the link let to this page.
The first two blogs (Cupcakes! and ASCII Fun!) were last year’s clues and the third was from this challenge. Had we only checked last year’s site, we may have solved this puzzle in minutes instead of days. Then again, we would have missed the fantastic video and the rest of the fun and we never would have learned so much about our good friend Kevin!
Thanks to the Verizon RISK Team for the challenge — we’re looking forward to next year!
— Mike (@SecuritySift), Andy (@Blackjack988) and William (@laughingwill).
 Security Sift
Security Sift