Testing Optionsbleed
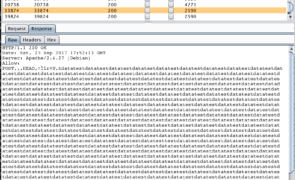
Introduction I took a few minutes to test the Optionsbleed vuln (CVE-2017-9798), specifically to see whether modifying the length and/or quantity of Options/Methods in the .htaccess file would enable me to extract anything of substance from memory. Ultimately it seems that by modifying the length of the entries in the .htaccess file, I was able to gain access to hundreds of bytes of POST data of a different virtual host. Note: Since originally…
Read more...Tags:apache , CVE-2017-9798 , exploit , htaccess , Optionsbleed , vulnerability
An Analysis Of MS15-034
are closed
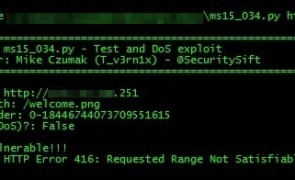
Introduction By now you’ve undoubtedly heard about MS15-034. The following is a collection of my cursory research and thoughts on this vulnerability. In addition, here is a small list of related resources, some of which I also reference in the sections that follow: Microsoft Security Bulletin MS15-034 (Microsoft) The Delicate Art of Remote Checks – A Glance Into MS15-034 (Beyond Trust) MS15-034: HTTP.sys (IIS) DoS And Possible Remote Code Execution. PATCH…
Read more...Tags:http , http.sys , ms15_034 , ms15-034 , phishing , python , range , range header , rce , remote code execution , shellshock
Drupal 7 SQL Injection (CVE-2014-3704)
are closed
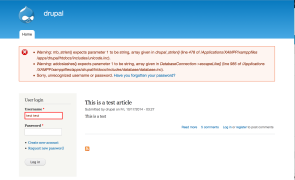
Introduction This vuln has been getting a lot of attention, and rightfully so. The good news is an update is available (and a supplemental patch has been released as well). The bad news is that it’s pre-auth SQLi. The basic problem is the way Drupal core 7.x versions prior to 7.32 construct a SQL query. Contrary to some claims, this is not a flaw in the use of prepared statements/parameterized queries, which…
Read more...Tags:cve , CVE-2014-3704 , drupal , exploit , injection , poc , proof of concept , sql , sql injection , sqli
Phishing for Shellshock
are closed
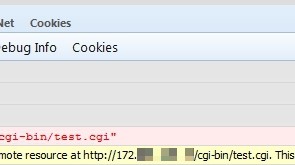
Introduction I thought I was done writing about Shellshock, but a recent discussion with some colleagues got me back on the topic. We were commenting about how organizations tend to react very quickly to patching external assets for a bug like Shellshock but many probably wait to patch internal assets due to a false sense of security. It got me thinking about how an external actor could exploit a bug like…
Read more...Tags:exploit , JavaScript , phishing , scan , shell , shellshock , shock , vulnerability
Shellshock – Targeting Non-CGI PHP
are closed

I’ve seen debates as to whether or not it’s possible to have an unpatched PHP server running in mod_php mode (i.e. not CGI) that is vulnerable to Shellshock. From my testing, the answer appears to be Yes…with some prerequisite conditions. First, the PHP application would have to be using Bash for its system commands — exec(), passthru(), system(), popen(), etc. This is pretty obvious since Shellshock is a Bash-specific vulnerability. Although PHP system command…
Read more...Why Google Makes My Job More Difficult
are closed
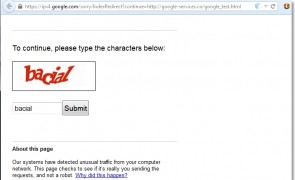
Let me start this post by saying I’m a huge Google fan. I use multiple Android devices and like many others, I’ve become an avid user of services such as Gmail, Docs, Maps, Photos, and Youtube. I even find myself fondly reminiscing about discontinued services such as Reader. And, if you’re like me, Google search has become an instrumental tool in your professional endeavors. So please keep in mind, this post is…
Read more...Tags:docs , google , google docs , phishing , redirection , redirector , redirects , unvalidated redirects
Understanding WordPress Auth Cookies
are closed
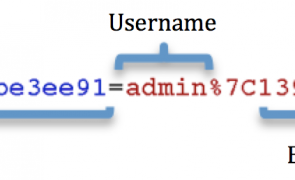
Introduction A recently published vulnerability prompted me to take another look at the wp_validate_auth_cookie WordPress function which is responsible for validating authenticated user requests and ultimately controls access to to your WordPress installation. This post is not about that specific vulnerability (more info here) but rather about how WordPress generates and validates authentication cookies to authorize user requests. If you’re a WordPress user, I encourage you to read on to see what stands between malicious actors and…
Read more...Tags:authentication , brute force , cookie , hash , key , password , salt , secret , wordpress , wp_validate_auth_cookie
Passive Reconnaissance
are closed
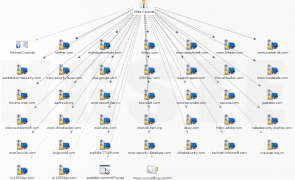
Introduction Recently, while watching the House Committee hearings on the security of Healthcare.gov, I was disappointed to hear testimony likening passive reconnaissance to a form of unauthorized/illegal activity that involved potentially invasive actions such as port/vulnerability scanning. To the contrary, passive recon can be one of the most useful and unobtrusive methods of data gathering for any penetration test or security assessment. In this post I outline what passive reconnaissance…
Read more...Tags:advanced search , burp , burpsuite , exploit-db , ghdb , google , google hacking , healthcare.gov , maltego , nerdydata , passive , passive recon , passive reconnaissance , pastebin , recon , reconnaissance , security , shodan
How NOT To Restrict Cross-Domain Flash Content
are closed
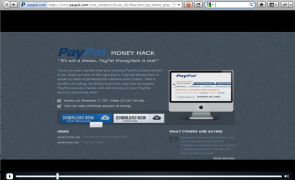
Introduction Insufficient input validation is a problem I encounter practically every time I test an application. I’ve talked about relying on input validation as a prevention mechanism before (see here and item #8 here) but since it’s such a prevalent problem I figured I’d take the time to write about it once again. While a good supplemental control, by itself input validation is usually woefully inadequate. Quite frankly, it often requires much…
Read more...Tags:bounty , bug bounty , cross domain , crossdomain , flash , jpexs , paypal
Bug Bounty Blitz!
are closed

Introduction Over the last couple of years it seems bug bounties have gained increased attention and are being embraced by more organizations — and for good reason. For companies, it can provide a cost-effective means of obtaining professional security testing and for the security community, any form of sanctioned testing against a live/production application is a good thing :). In May of this year I decided to undertake a little…
Read more...Tags:bounties , bounty , bug bounties , bug bounty , bug bounty program , bugcrowd , bugs
 Security Sift
Security Sift
are closed