Offensive Security’s PWB and OSCP — My Experience

Overview Recently I took the Offensive Security Penetration Testing with Backtrack (PWB) course, passed the exam, and achieved the OSCP certification. I learned a ton and earned my most rewarding cert yet. There are several great reviews of the course but I figured I’d provide my perspective. Motivations In my current job I’m lucky enough to touch on all aspects of information security from policy and process development to application…
Read more...Tags:Backtrack , class , course , enumeration , Kali , Offensive Security , Offsec , OSCP , pen testing , penetration testing , pentest , privilege escalation , PWB
Who do you trust? Cross-domain content extraction with Clickjacking
are closed

Overview Today I’ll illustrate how it’s possible to extract sensitive data via Clickjacking by taking advantage of some liberal framing behaviors in Firefox coupled with a X-Frame-Options:Allow header that forms an implicit trust relationship between two sites. This Clickjacking POC takes advantage of several site and browser behaviors including: Etsy.com set an X-Frames-Options: Allow header when accessed directly from a search engine query result Microsoft Bing search engine allows framing…
Read more...Tags:Bing , Clickjacking , content extraction , cross domain , Etsy , Firefox , trust , X-Frame-Options
Solving the AusSHIRT 2013 Sophos Puzzle
are closed
Intro This was a fun little puzzle that served as a quick brain-teaser/diversion a short while back. I didn’t see this puzzle when it was first announced but eventually noticed it on Twitter so I got a bit of a late start. Several people had already solved it when I began, one of them using Notepad. I didn’t feel like writing yet another script so I figured why not try…
Read more...When is Clickjacking NOT a concern?
are closed
According to Microsoft, when it involves more than 1 click. That’s the feedback I received when I recently submitted a Clickjacking bug to Microsoft’s Security team. This particular Clickjacking bug, on an authenticated portion of the site, could induce a victim to unknowingly change their account privacy settings. The problem, according to Microsoft, is that it requires a minimum of two clicks; one to change the privacy setting and one…
Read more...Tags:bug bounty , Clickjacking , Microsoft , web security , X-Frame-Options , XFO
11 Fallacies of Web Application Security
are closed

Introduction By far, application security testing is one of the best parts of my job. Working one-on-one with application developers, I find that nearly all want to do the right thing when it comes to security but many face common misconceptions about security vulnerabilities (and the necessary remediation actions). This is my attempt to address some of those misconceptions surrounding authentication, session management, access control, SQL Injection, XSS, and CSRF…
Read more...Tags:authentication , csrf , injection , session management , web application security , XSS
Solving the 2013 Verizon DBIR Cover Challenge
are closed

Intro Each year the Verizon RISK Team releases its highly anticipated Data Breach Investigations Report (DBIR) — download this year’s report here. For some of us, equally as exciting as the content of the report is the DBIR Cover Challenge — a multi-stage puzzle that requires participants to follow obscure (and often hilarious) clues, testing their critical thinking and problem solving skills along the way. Following two consecutive fourth place…
Read more...Tags:Data Breach Investigations Report , DBIR , haberdasher , puzzle , Verizon RISK Team
Quotes and XSS — Planning Your Escape
are closed
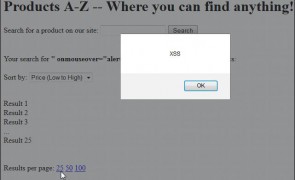
Introduction It’s been my observation that when it comes to XSS prevention, angle brackets associated with HTML and script tags (<>) often get the majority of the attention. While eliminating script tags as a potential XSS vector is a great start, just as important, and seemingly most forgotten when it comes to input validation and output encoding, are double (“) and single (‘) quotes. Whether they are completely ignored or…
Read more...Tags:Cross Site Scripting , encoding , escaping , filter evasion , input validation , penetration testing , quotes , reflected xss , security , web application , web security , XSS
Cross Origin Request Forgery Pt 2 – Exploiting Browser Security
are closed
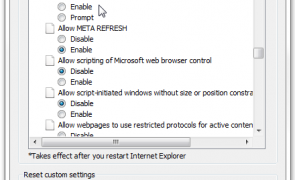
Introduction In my previous post I demonstrated how insecure handling of CSRF tokens by applications that switch between HTTP and HTTPS can put users at risk of request forgery attacks via man-in-the-middle interception. Today I ‘ll expand upon this point and demonstrate how it can provide remote attackers the same opportunity, if the user’s browser is not configured to prevent insecure cross-domain communications. Recall in the last post, the site…
Read more...Tags:browser security , cross domain , cross origin , cross site request forgery , csrf
Cross Origin Request Forgery – Attacking HTTPS via HTTP MiTM Injection
are closed
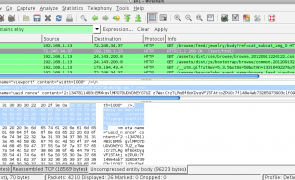
Introduction There are several scenarios in which a web application may choose to deliver both HTTP and HTTPS content. It may employ per-page mixed content, it may use HTTP pre-auth and switch to HTTPS post-auth, or it may continually switch back and forth between HTTP and HTTPS depending on the sensitivity or criticality of the functions being performed by the user (i.e. browsing media content vs. making online purchases). For…
Read more...Tags:csrf , http injection , mitm , request forgery , session management , web security
Not your breach, but still your concern
are closed

Why your organization should be concerned with others’ breaches. It seems we’re constantly reading about breaches that result in the leak of login credentials–Gawker, Toshiba, Sony, Yahoo, LinkedIn…this list goes on. Just this week ArenaNet (developers for Guild Wars 2) announced they are experiencing account hacks believed to be facilitated by the use of password lists stolen from other games and sites. Many organizational executives or security personnel might read about these…
Read more... Security Sift
Security Sift
are closed