Abusing Microsoft Office DDE
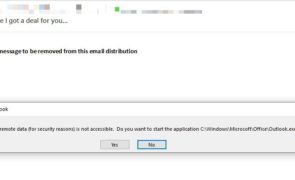
Introduction Earlier this month I came across a post by the team at SensePost outlining their macro-less code execution technique using the antiquated DDE feature of Microsoft Word. As you may be aware, this feature has existed in Office for many years and was even written about over 15 years ago as a potential threat vector. Old or not, as we continue to put up obstacles in front of malicious actors…
Read more...Tags:dde , ddeauto , dynamic data exchange , Microsoft , Microsoft Word , office , outlook , phishing , word
Testing Optionsbleed
are closed
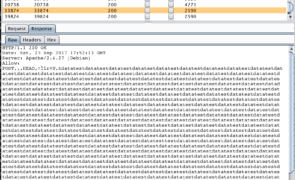
Introduction I took a few minutes to test the Optionsbleed vuln (CVE-2017-9798), specifically to see whether modifying the length and/or quantity of Options/Methods in the .htaccess file would enable me to extract anything of substance from memory. Ultimately it seems that by modifying the length of the entries in the .htaccess file, I was able to gain access to hundreds of bytes of POST data of a different virtual host. Note: Since originally…
Read more...Tags:apache , CVE-2017-9798 , exploit , htaccess , Optionsbleed , vulnerability
ASK/L(OOK)/Listen! – Basic Signal Decoding and Replay
are closed
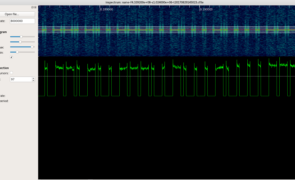
Introduction It’s been quite a while since my last post and I figured it was time to start contributing again so I’m kicking it off with a quick-and-dirty method to decode and replay ASK On-off keying (OOK) signals. A couple of notes before I delve in… First, this is not intended to be an intro to SDR/RF hacking. If you’re new to the subject, I highly recommend you go through Michael Ossmann’s free video…
Read more...Tags:ask , decode , inspectrum , on-off-keying , ook , osmocom , osmocom_fft , rfcat , yardstick one
Phishing with Macros and Powershell
are closed
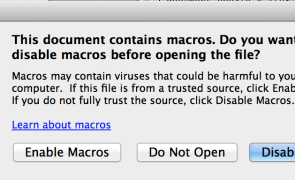
Over the past 6 months, it seems we’ve been experiencing a resurgence of macro-based malware, possibly because it’s such a simple and proven means of delivering a phishing payload to large organizations. If you’re performing a penetration test against an organization and you have reason to believe untrusted macro execution is enabled, they can also be a good means to test user awareness and gain a foothold via social engineering. Regardless of their popularity,…
Read more...Tags:email , exchange , exploit , macro , Microsoft , microsoft office , office , phishing , powershell
Offensive Security’s CTP and OSCE – My Experience
are closed
Overview I had been wanting to take the Cracking The Perimeter (CTP) course for some time but my schedule was pretty hectic. I finally forced myself to start it at the beginning of the new year and I’m really glad I did. As promised, here is my review… Prerequisites Offsec states the following: Many pre-requisites are required, such as good familiarity with a Ollydbg, and a general mastery of offensive network security techniques. Definitely sound advice….
Read more...Tags:certification , cracking the perimeter , ctp , Kali , Offensive Security , Offsec , osce , OSCP , penetration testing , security
An Analysis Of MS15-034
are closed
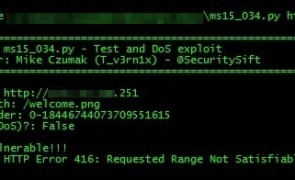
Introduction By now you’ve undoubtedly heard about MS15-034. The following is a collection of my cursory research and thoughts on this vulnerability. In addition, here is a small list of related resources, some of which I also reference in the sections that follow: Microsoft Security Bulletin MS15-034 (Microsoft) The Delicate Art of Remote Checks – A Glance Into MS15-034 (Beyond Trust) MS15-034: HTTP.sys (IIS) DoS And Possible Remote Code Execution. PATCH…
Read more...Tags:http , http.sys , ms15_034 , ms15-034 , phishing , python , range , range header , rce , remote code execution , shellshock
peCloak.py – An Experiment in AV Evasion
are closed
Introduction I just wrapped up the Offensive Security Cracking The Perimeter (CTP) course and one of the topics was AV evasion. Although I write a lot of custom scripts and tools, when it comes to AV evasion, I typically rely on the tools and methods of others (Veil, powershell, python, custom shellcode). That said, the great thing about courses like CTP is they give me an excuse to investigate a topic that I haven’t…
Read more...Tags:anti-virus , antivirus , av , av evasion , Avast , AVG , Avira , Bitdefender , BullGuard , code cave , Comodo , detection , ESET , evasion , heuristics , Kaspersky , malware , Malwarebytes , McAfee , metasploit , Microsoft , Panda , peCloak , pefile , pydasm , python , SectionDoubleP , Spybot , symantec , Trend Micro , virus
EggSandwich – An Egghunter with Integrity
are closed

Introduction A while back I introduced the EggSandwich in my tutorial on Egghunting as a means to implement some basic integrity checks into the traditional Egghunter and overcome the problem of fragmented / corrupted shellcode. I recently took the opportunity to update my implementation so it could accomodate shellcode of any size. The code and a brief explanation follows. What is the EggSandwich? I ran into a situation when developing an exploit for an…
Read more...Developing a Security Assessment Program
are closed
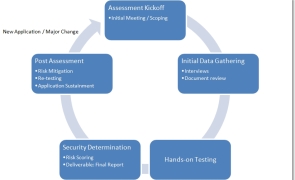
Introduction Most organizations and are deploying new applications and technologies at a high rate and without a means to adequately assess them prior to implementation, it’s difficult to accurately gauge your organization’s risk. No matter what the size or industry, it’s imperative that an organization has a standardized and repeatable process for assessing the security of the IT solutions it implements. My goal with today’s post is to provide some recommendations on…
Read more...Tags:application security , assessment , nist , penetration testing , pentesting , risk , risk management
Exploiting MS14-066 / CVE-2014-6321 (aka “Winshock”)
are closed
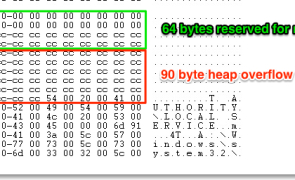
Introduction I think enough time has passed now to provide a little more detail on how to exploit MS14-066 schannel vulnerability (aka “Winshock”). In this post I won’t be providing a complete PoC exploit, but I will delve into the details on exactly how to trigger the heap overflow along with some example modifications to OpenSSL so you can replicate the issue yourself. This vulnerability was announced while I was on…
Read more... Security Sift
Security Sift
are closed