Testing Optionsbleed
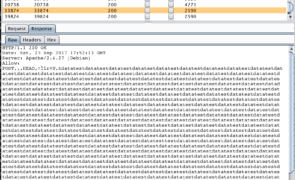
Introduction I took a few minutes to test the Optionsbleed vuln (CVE-2017-9798), specifically to see whether modifying the length and/or quantity of Options/Methods in the .htaccess file would enable me to extract anything of substance from memory. Ultimately it seems that by modifying the length of the entries in the .htaccess file, I was able to gain access to hundreds of bytes of POST data of a different virtual host. Note: Since originally…
Read more...Tags:apache , CVE-2017-9798 , exploit , htaccess , Optionsbleed , vulnerability
ASK/L(OOK)/Listen! – Basic Signal Decoding and Replay
are closed
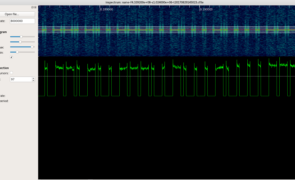
Introduction It’s been quite a while since my last post and I figured it was time to start contributing again so I’m kicking it off with a quick-and-dirty method to decode and replay ASK On-off keying (OOK) signals. A couple of notes before I delve in… First, this is not intended to be an intro to SDR/RF hacking. If you’re new to the subject, I highly recommend you go through Michael Ossmann’s free video…
Read more...Tags:ask , decode , inspectrum , on-off-keying , ook , osmocom , osmocom_fft , rfcat , yardstick one
 Security Sift
Security Sift
are closed