Google
Current archive: October 21, 2012
Cross Origin Request Forgery Pt 2 – Exploiting Browser Security
Written on:October 21, 2012
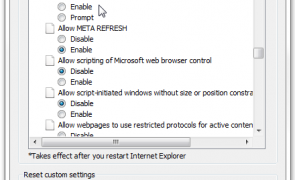
Introduction In my previous post I demonstrated how insecure handling of CSRF tokens by applications that switch between HTTP and HTTPS can put users at risk of request forgery attacks via man-in-the-middle interception. Today I ‘ll expand upon this point and demonstrate how it can provide remote attackers the same opportunity, if the user’s browser is not configured to prevent insecure cross-domain communications. Recall in the last post, the site…
Read more...In category: Web Security
Tags:browser security , cross domain , cross origin , cross site request forgery , csrf
Tags:browser security , cross domain , cross origin , cross site request forgery , csrf
 Security Sift
Security Sift
are closed